Difference between Session and JWT Authentication

In today's world, keeping our online accounts secure is our topmost priority. When it comes to verifying user identities in web applications, there are two common methods: JSON Web Tokens (JWT) and session-based authentication. Although they serve the same purpose, they work differently. In this blog post, we'll explore the differences between JWT and session-based authentication, and understand when and why each method is used.
What is Authentication?
Before knowing about the difference between these two authentication methods, we need to understand what exactly is authentication. Authentication is basically the process of verifying the identity of an individual, (in some cases it can be a system) to determine whether access should be granted to a particular service or not. It typically involves the presentation of credentials, such as usernames, email, phone numbers and passwords, to authenticate the identity of that particular user.
Introduction to JWT Authentication & JWT Structure
JSON Web Tokens (JWT) is an open standard (RFC 7519) that provides a compact and self-contained way to transmit information securely between parties as a JSON object. JWTs are widely used for authentication and authorization in modern web applications and APIs.
A JWT consists of three main parts: the header, the payload, and the signature. The header contains metadata about the token, such as the algorithm used for signing. Consider it as an “Id card”. The payload carries claims, which are statements about an entity (typically the user) and additional data. It is like the personal information section on the card, where details like name, age, and address are stored. Finally, the signature is created by combining the encoded header, payload using a secret key, which ensures the integrity of the token. Think of it as the “official stamp” on an Id Card.
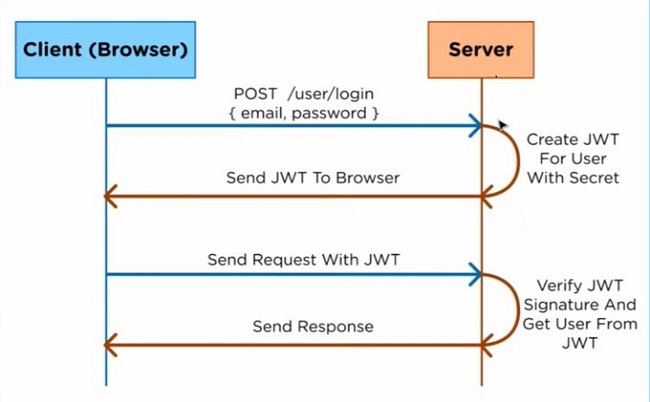
How JWT Authentication Works:
When a user logs in successfully, the server generates a JWT containing relevant information about the user. This JWT is then sent back to the client and stored, typically in local storage or a cookie. On subsequent requests, the client includes the JWT in the request headers. The server validates the JWT, ensuring its integrity and verifying the user's identity, before granting access to protected resources.
Introduction to Session-Based Authentication:
Session-based authentication is a traditional approach that relies on server-side sessions to authenticate and authorize users. In this method, a session ID is generated upon successful authentication and is used to track the user's session throughout their interactions with the application.
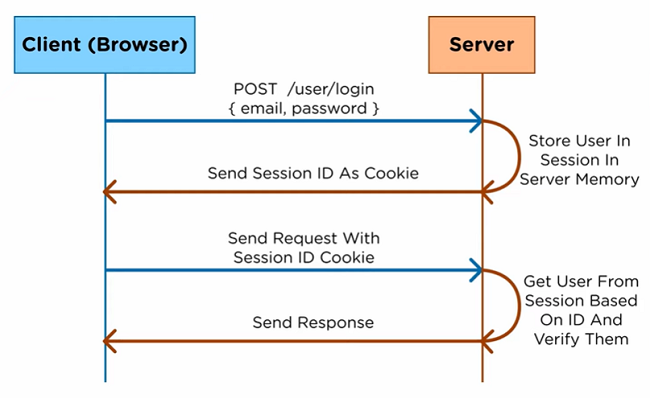
How Session-Based Authentication Works:
When a user logs in, the server creates a session for that user and assigns a unique session ID. This session ID is then stored on the server in memory or database and sent back to the client as a cookie. The client includes this session ID in subsequent requests, allowing the server to retrieve the associated session data and authenticate the user.
Session Management:
Session management is an essential aspect of session-based authentication. The server must store session data securely and associate it with the correct user. Typically, session data is stored in memory, databases, or distributed cache systems. The server needs to handle session expiration, session revocation, and session fixation attacks to ensure the security and integrity of the sessions.
Key Differences Between JWT and Session-Based Authentication
Now let's examine the differences between JWT and session-based authentication in several important aspects.
Statelessness vs. Statefulness:
JWT authentication is stateless, meaning that the server does not need to maintain any session data. All the necessary information is contained within the JWT itself, allowing for easier scalability and reduced server-side storage requirements. On the other hand, session-based authentication relies on server-side sessions, which require storing session data on the server and maintaining state between requests.
Scalability and Performance:
Due to their stateless nature, JWTs are highly scalable. The server does not need to perform any database lookups or session management tasks, resulting in improved performance and reduced server load. Session-based authentication, while effective for smaller applications, may face scalability challenges as the number of active sessions increases.
Security and Revocation:
JWTs are signed using a secret key, ensuring their integrity and protecting against tampering. However, revoking JWTs before they expire can be challenging since they are self-contained. In contrast, session-based authentication allows for easy session revocation since the server maintains control over session data.
JWT tokens are mostly stored in local storage and it is accessible by third pary. This may lead to man-in-the-middle attack. In case of Session based auth, session ID is stored as cookie and it can be accessed only by the application.
Cross-Origin Resource Sharing (CORS) Support:
JWTs are suitable for cross-origin resource sharing (CORS) scenarios. Since JWTs are sent with each request, they can be used to authenticate API requests from different domains. Session-based authentication, on the other hand, relies on cookies, which can be subject to cross-site scripting (XSS) attacks when used across different domains.
Implementation Complexity:
JWT authentication requires additional implementation effort, as the server needs to validate the signature and extract the necessary information from the token on each request. Session-based authentication, while simpler to implement, requires session management and handling of session data on the server.
Use Cases where Session-Based Authentication can be used:
E-commerce Websites: Session-based authentication is often used in e-commerce websites where users need to log in to their accounts to view personalized product recommendations, access order history, and manage their shopping carts. The server maintains session data to keep track of user interactions throughout the shopping session.
Online Banking: In the banking sector, session-based authentication is widely used to ensure secure access to online banking services. When a user logs in, a session is created, allowing them to perform various financial transactions and access sensitive account information within that session. The session is typically terminated after a period of inactivity or upon user logout.
Use Cases where JWT Authentication can be used:
Single Sign-On (SSO) Systems: JWT authentication is commonly used in Single Sign-On systems, where a user logs in once and gains access to multiple applications or services. The user's authentication is verified through a JWT, which is shared among the different services. This eliminates the need for multiple authentication processes, enhancing user experience and security.
Mobile Applications: JWT authentication is well-suited for mobile applications, including both native apps and hybrid apps built with frameworks like React Native. Mobile apps often communicate with backend APIs to retrieve data or perform actions on behalf of the user. JWTs are used to authenticate API requests, allowing secure access to resources without the need for session management.
Social Media Applications: JWT authentication is suitable for social media applications that offer APIs to integrate with third-party services or provide data to other applications. By using JWTs, users can grant access to their social media accounts for specific actions without sharing their actual credentials. The JWT ensures secure authentication and authorization for API requests.
Conclusion
In summary, JWT and session-based authentication offer distinct approaches to verify user identity in web applications. JWTs are highly scalable and suitable for stateless scenarios, while session-based authentication provides greater control over sessions and revocation. Understanding the differences between these authentication methods is crucial for selecting the appropriate approach based on your application's requirements. By making an informed choice, you can ensure secure and efficient authentication for your users.

