The 5 Phases of Ethical Hacking

The word hacking means getting the access of someone's computer, network etc for rational or irrational purposes. So if we consider there are 5 phases of hacking.
- Passive scanning / Reconnaissance / Recon
- Active scanning / Enumeration
- Gaining access
- Maintaining access
- Clearing/covering track
Passive scanning / reconnaissance / recon
In this phase the attacker tries to gather information about the target without directly interacting with the target. This is done by not infiltrating the target but by gathering information from outside the target system, network,etc by using any other kinds of tools. The tools used for this phases are:
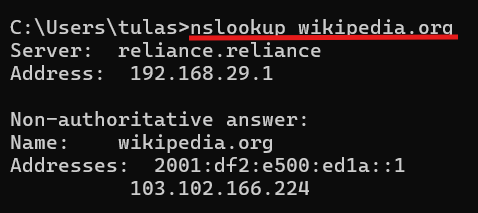
Nslookup
It is a command line tool used to obtain the mapping of domain name and IP address, and other DNS records. It is like a ping service but the ping service refers to the OS’s resolution and nslookup retrieves the default DNS server address.
Shodan
Shodan is just a simple search engine that find information about various devices connected to the internet such as webcams, routers, and servers. It was created by john matherly in 2009 as a hobby. User can search for device on basis of region, country, hostname etc.
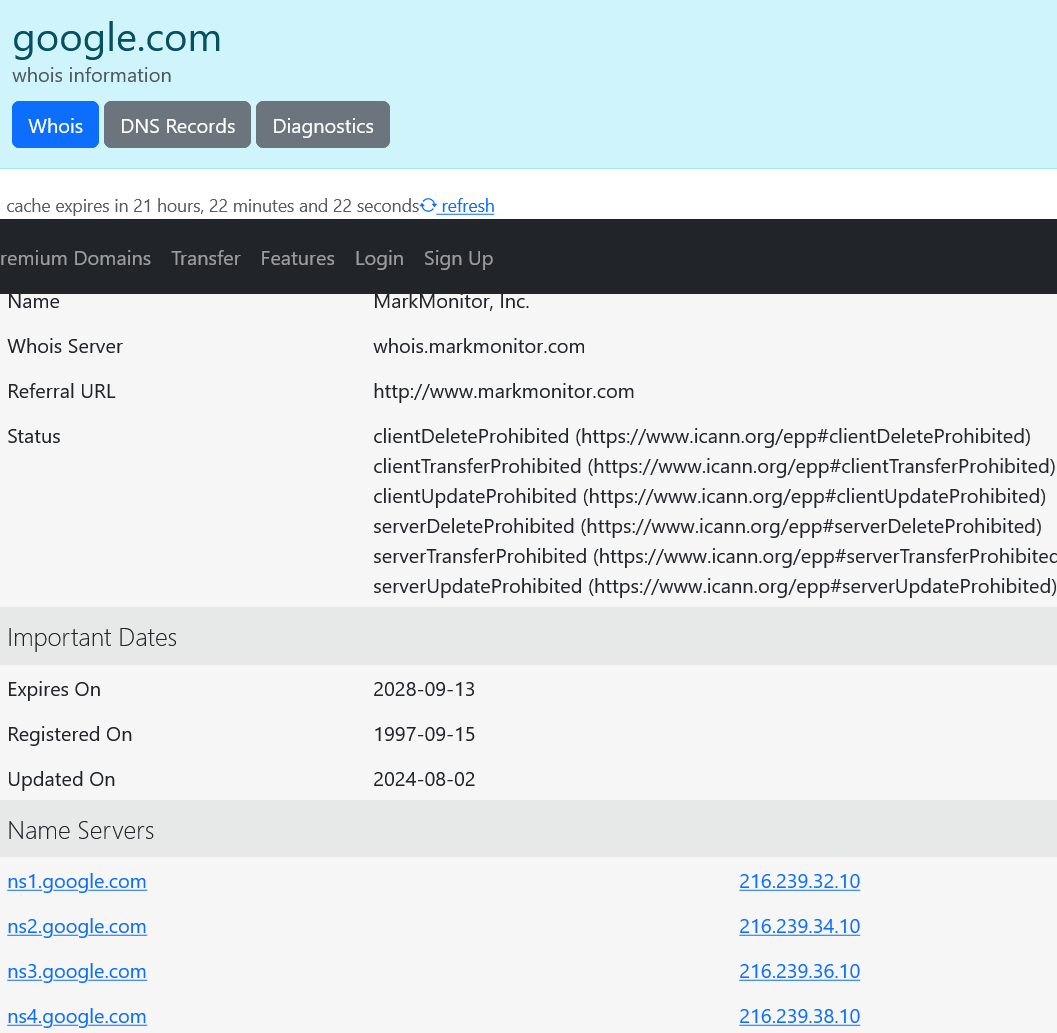
Who is
It is a query and response protocol that help you to find out about the owner of any domain and also it can trace the website issues . It contain the information such as the owner’s name, address ,phone number ,email address etc.
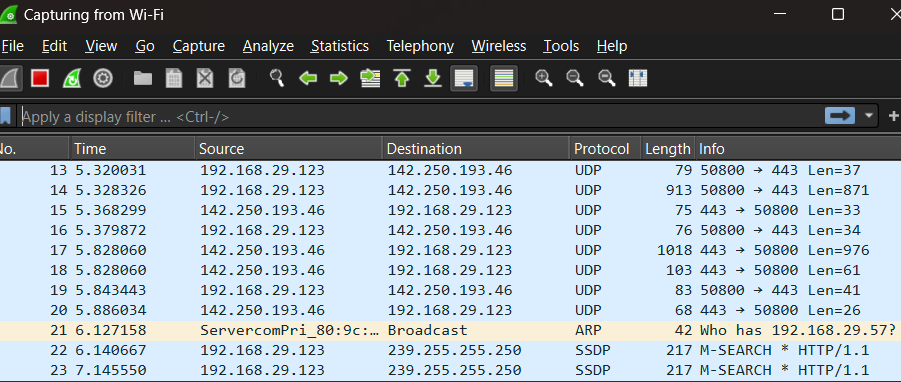
Wireshark
Wireshark is a tool use to monitor to the network traffic that we can use to get any data that is transfered through the network. We can also get the IP and MAC address of any device accessing the network. With the help of wireshark we can do ARP spoofing.
It is a normal search engine that we use in our day to day life we can read articles and news about the target (if any posted online) and plan our strategies for the exploits.
The main advantage of this process is that the target will never know that someone is gathering information about them. But with the recon only we can't get an idea for cracking the system. We have to do an enumeration for more juicy information.
Active scanning / Enumeration
In this phase the attacker tries to gather information about the target directly interacting with the target. This is done by entering the target infrastructure, website, network to check what are the vulnerable points or parts present in the target system. This is done with the help of enumeration tools such as:
Nmap
Nmap stands for network mapper. It is an open source linux based tool scan the network of any IP and website. Nmap is a powerful tool for scanning for vulnerabilities and identifying potential risks to your network. It contains a host of commands, and a versatile scripting engine with many included and downloadable scripts which can be combined into precision scanning or automated for broad results. To check open ports we can use command:
nmap -A <target website> / <target ip>Here -A is for aggressive scan.

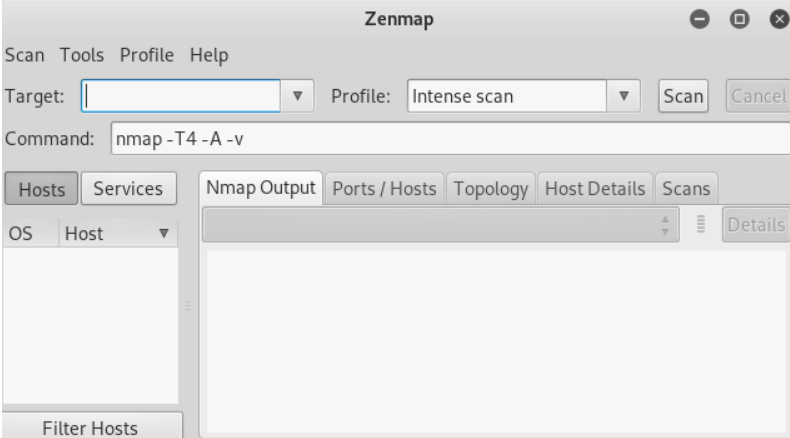
Zenmap
Zenmap is a GUI version of nmap that is supported in linux,windows etc.it works same as nmap but with a graphical interface. It is made for beginner learners for visual benefits and it can give result in both text and graphical format.
Nessus
Nessus is a vulnerability scanner that scans a network or device and give out the possible results of any flaws present in the network or device. It is different from the nmap because nmap scan host and services. Nessus has a graphical interface that help us to understand the results easily. It is developed by tenable for mainly industrial network but if you know how to use nmap it can give better results than Nessus.
Metasploit
Metasploit framework that make hacking simple for both attacker and defender. It is the world’s leading penetrating framework use for both offensive and defensive security. There are many exploits present in msfconsole by which we can learn how the hackers attack the system.
Wireshark
The enumeration can be caught and prevented. But it provides very juicy and valuable information about the victims so it is an important phase and can't be neglected.
Gaining access
It is the most important and vital phase from all the phases. In this phase the attacker gains the access of the target system by the help of vulnerability found from the active and passive scanning. For example, an ethical hacker that identifies open ports (20, 21) on the target during the scanning phase may be able to exploit the FTP service to plant malware. For vulnerability exploitation, the Metasploit Framework is one of the most famous and commonly used tools. Here are the tools used for gaining access:
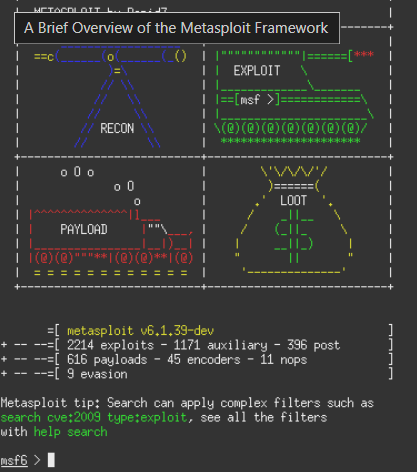
Burp Suite
Burp Suite is an application security testing software. At a most basic level, you can open a "Burp" browser and any requests / responses will be "proxied" through to the Burp application. This tool is common among red teams for breaking into sites, and blue teams for scanning sites.
Sqlmap
Sqlmap is an open source penetration testing tool which scan and exploits SQL injection flaws. The goal is to detect and take advantage of SQL injection vulnerabilities in web applications.
Maintaining access
After getting access to the target machine the main process started. First we have to maintain access and create a backdoor so that whenever we want we can exploit the target machine. The malware or RAT(remote access tools) such as Stitch can be used to create backdoors.
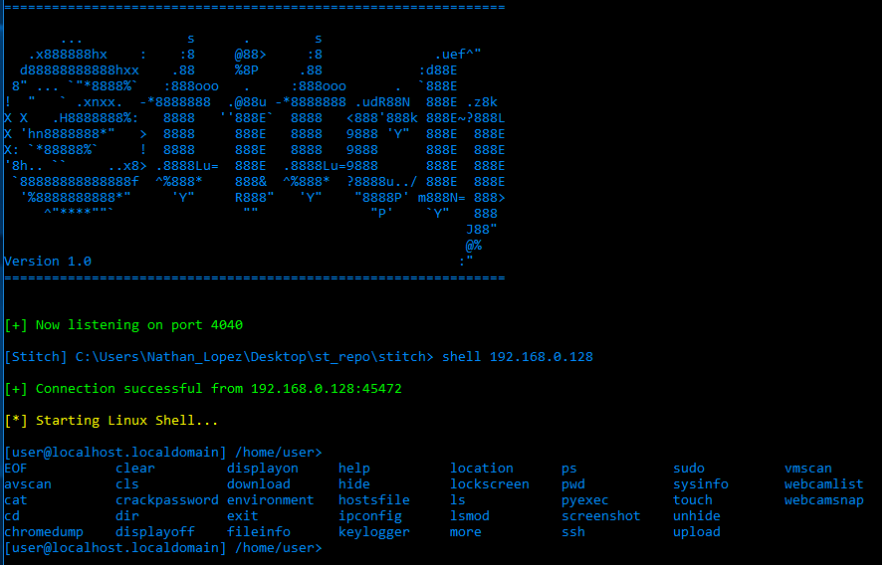
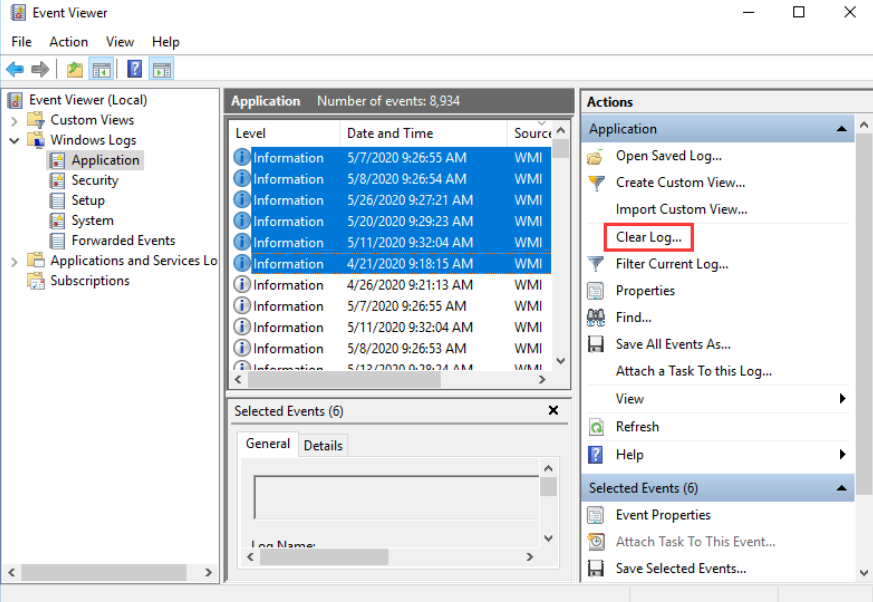
Clearing / Covering track
It is very important for the safety of hackers to cover its tracks. It is the final phase of a successful hack, where hackers remove the traces of their presence that could reveal their identity or action.
We can clear the tracks by
Tampering log files
Closing open ports
We can use the command to get process details which has opened the port and kill the process using kill command.
netstat -ltnup
Remove malicious malware
By deleting the malware installed we can cover our tracks. It will become difficult to catch the attacker who knows how to clear their footprints.
Conclusion
While not every hacker follows these steps in order, they offer a systematic approach that yields better results. Most of the time is spent on the Reconnaissance process. Time spent gets reduced in upcoming phases.
As technology is developing, hacking technology is also developing . Staying informed and careful is key to securing systems against these sophisticated multi-phase attacks.
The purpose for hacking may include alteration of a system’s resources or disruption of features and services to achieve other goals. Hacking can also be used to steal confidential information for any use, such as sending it to competitors, regulatory bodies, or publicizing it.

